|
Size: 1727
Comment:
|
Size: 2313
Comment:
|
| Deletions are marked like this. | Additions are marked like this. |
| Line 1: | Line 1: |
| #rev 2020-09-09 bonaccos <<TableOfContents(4)>> |
|
| Line 3: | Line 7: |
| If you're connecting the first time to a SSH Server you will perhaps get an alert message. The fingerprint should also be shown right below the message. | If you're connecting the first time to a SSH Server you will get an alert message. The fingerprint should also be shown right below the message. Key point is that you '''always need''' to verify the fingerprint of the remote server before proceeding with the first login. |
| Line 5: | Line 9: |
| ==== Windows ==== | == Linux == {{attachment:linux.jpg}} /!\ Be aware that the "." (dot) at the end of the fingerprint is not part of the key fingerprint. == Windows == |
| Line 8: | Line 17: |
| ==== Linux ==== {{attachment:linux.jpg}} |
== The website == |
| Line 11: | Line 19: |
| /!\ Be aware that the "." (dot) at the end of the fingerprint is not part of they key. | You can check if the fingerprint is correct trough a second (secured/trusted) channel on this website (https://ssh-fingerprints.ee.ethz.ch/) for ISG.EE managed hosts. |
| Line 13: | Line 21: |
| ==== The website ==== You can check if the fingerprint is correct with this website (https://ssh-fingerprints.ee.ethz.ch/). The website contains the SSH fingerprints of every SSH server we manage. |
The website contains the SSH fingerprints of every SSH server ISG.EE manage. |
| Line 19: | Line 24: |
| Line 20: | Line 26: |
| Line 21: | Line 28: |
| If it's the same fingerprint as shown then you can safely trust the connection. | If it's the same fingerprint as shown then you can accept to trust the server and proceed. |
| Line 25: | Line 33: |
| There may be more than one ssh-key for one host. ssh-ed25519 has stronger encryption than ssh-rsa but ist not yet widely supported. | There may be more than one ssh-key for one host. ssh-ed25519 has stronger encryption than ssh-rsa, but it might not yet be supported by your SSH client. |
| Line 27: | Line 35: |
| There also is a md5 and SHA256 version of every key. Windows uses the md5 and Linux the SHA256 one. | The website prints for every the fingerprint hash with MD5 and SHA256. By default nowdays Linux SSH clients uses/print the SHA256 fingerprint hash, on Windows only a MD5 fingerprint hash. |
| Line 29: | Line 37: |
| ==== Example for bad connection ==== | == Example for bad connection == |
| Line 32: | Line 40: |
| As you can see the name and the IP address is the same but the ssh key is not. You should not only check the hostname and IP address but most importantly the fingerprint. | As you can see the name and the IP address is the same but the SSH key is not. You should not only check the hostname and IP address but most importantly the fingerprint. |
| Line 34: | Line 42: |
| If come across this case please under no circumstances press yes and contact us immediately us at support@ee.ethz.ch | If you come across this case please '''under no circumstances''' type yes. '''Instead contact us immediately''' at <support@ee.ethz.ch>. == Example for correct connection == {{attachment:yes.png}} If the hostname, the IP address and especially the fingerprint matches with the one from our website then you can safely enter yes. |
Contents
SSH Fingerprints Website
If you're connecting the first time to a SSH Server you will get an alert message. The fingerprint should also be shown right below the message. Key point is that you always need to verify the fingerprint of the remote server before proceeding with the first login.
Linux
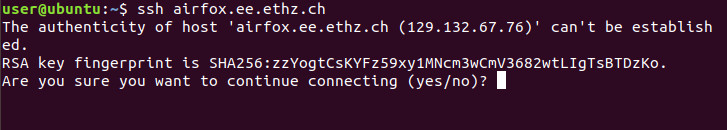
![]() Be aware that the "." (dot) at the end of the fingerprint is not part of the key fingerprint.
Be aware that the "." (dot) at the end of the fingerprint is not part of the key fingerprint.
Windows
The website
You can check if the fingerprint is correct trough a second (secured/trusted) channel on this website (https://ssh-fingerprints.ee.ethz.ch/) for ISG.EE managed hosts.
The website contains the SSH fingerprints of every SSH server ISG.EE manage.
Type in the hostname you want to connect to into the search bar on the top right corner of the website.
The host with its fingerprint should now be shown in the table.
Compare the fingerprint with the alert message.
If it's the same fingerprint as shown then you can accept to trust the server and proceed.
On the top left there is a button to show or hide the SSH-Keys. These keys are saved in a file so the system can be authenticated as a "known host". Upon clicking "Yes" on your first connection to a server, the connection will be saved in that file.
There may be more than one ssh-key for one host. ssh-ed25519 has stronger encryption than ssh-rsa, but it might not yet be supported by your SSH client.
The website prints for every the fingerprint hash with MD5 and SHA256. By default nowdays Linux SSH clients uses/print the SHA256 fingerprint hash, on Windows only a MD5 fingerprint hash.
Example for bad connection
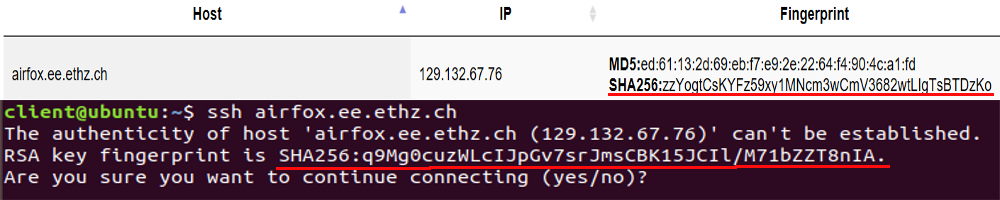
As you can see the name and the IP address is the same but the SSH key is not. You should not only check the hostname and IP address but most importantly the fingerprint.
If you come across this case please under no circumstances type yes. Instead contact us immediately at <support@ee.ethz.ch>.
Example for correct connection
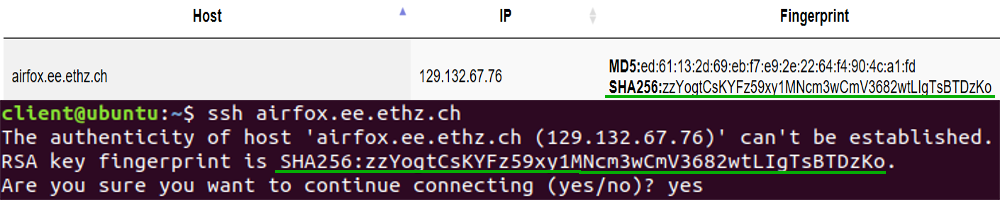
If the hostname, the IP address and especially the fingerprint matches with the one from our website then you can safely enter yes.